- Account Home
- Language
- News
- Products
-
Cases
By Service
- Help & Support
- Partners & Training
- About Us
ZStack provides VM instances with multiple network resources, including VPC firewall, security group, virtual IP address (VIP), elastic IP address (EIP), port forwarding, IPsec tunnel, load balancing, and flow monitoring.
Network Service Module provides a group of network services. Note that this module has been hidden on the UI.
Provides various network services: DNS, SNAT, load balancing, port forwarding, EIP, and DHCP.
ssh-key injection. By running cloud-init, these parameters will be loaded and injected into your VM instance when the VM instance is started. Note: The DHCP service includes the DNS feature.
Note: The DHCP service includes the DNS feature.ssh-key injection. By running cloud-init, these parameters will be loaded and injected into your VM instance when the VM instance is started. Note: The DHCP service includes the DNS feature.
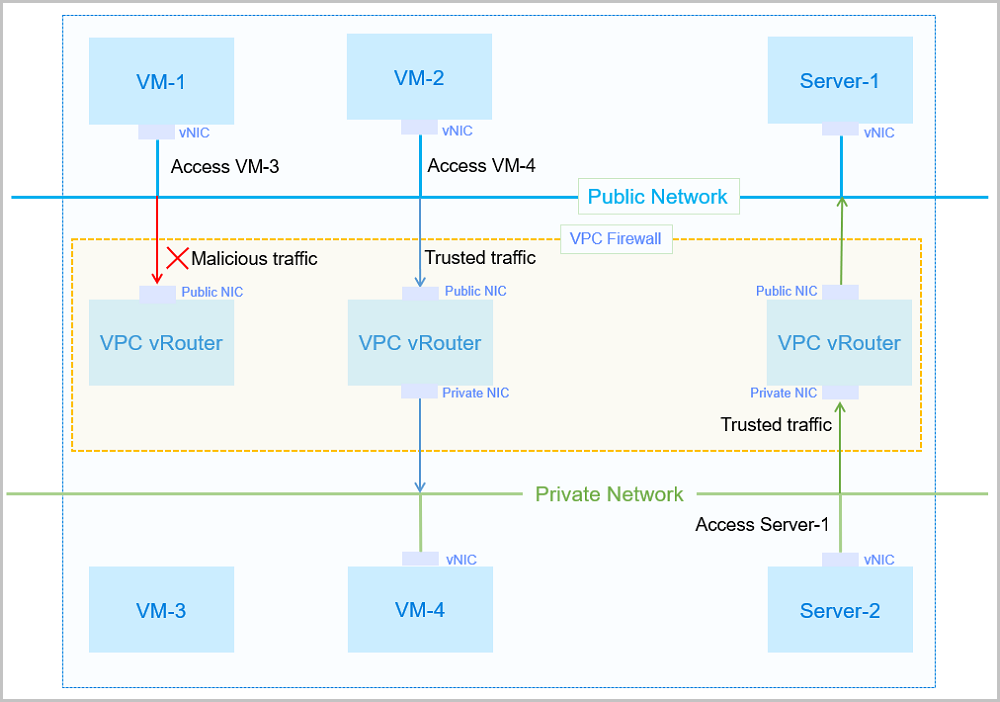
Note: The DHCP service includes the DNS feature.ssh-key injection. By running cloud-init, these parameters will be loaded and injected into your VM instance when the VM instance is started.ssh-key injection. By running cloud-init, these parameters will be loaded and injected into your VM instance when the VM instance is started.A VPC firewall manages the south-north traffics of VPC networks, and allows you to manage the access control policies by configuring rule sets and rules.
Each rule set only applies to inbound or outbound traffics, not both, in a VPC vRouter. That is, you can only add one inbound or outbound rule set to a VPC vRouter. A rule set contains multiple rules, which effectively secure the entire VPC communication and the VPC vRouter. This complements the security groups that can be applied to VM NICs and mainly protects the east-west communication security.
| Comparison | Security Group | VPC Firewall |
|---|---|---|
| Application scope | VM NIC | The entire VPC network |
| Deployment mode | Distributed | Centralized |
| Deployment location | VM instance | VPC vRouter |
| Configuration policy | Supports only allowed policies | Enables you to customize the accept policy, drop policy, or reject policy as needed |
| Priority | Takes effect according to the configuration sequence | Enables you to customize priorities |
| Matching rules | Source IP address, source port, and source protocol | Source IP address, source port, destination IP address, destination port, protocol, and packet status |
 Note: When you create a VPC firewall, make sure that the corresponding VPC vRouter is in the running state, and is not attached to any firewall.
Note: When you create a VPC firewall, make sure that the corresponding VPC vRouter is in the running state, and is not attached to any firewall.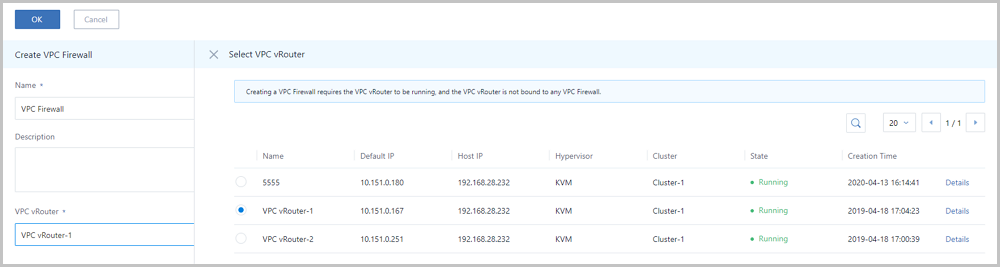
 Note:
Note: 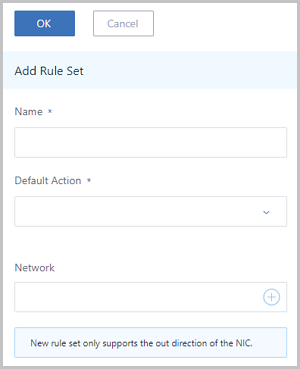
 Note:
Note: 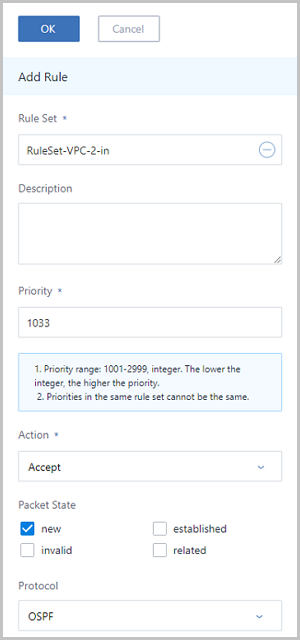
 Note: When you add a new network service, such as OSPF, to a VPC vRouter, some firewall rules will be created at the same time. However, these rules will not be displayed in the UI. To display the rules in the UI, click the update configuration button, and then the rules will be synchronized from the VPC vRouter to the database of the Cloud.
Note: When you add a new network service, such as OSPF, to a VPC vRouter, some firewall rules will be created at the same time. However, these rules will not be displayed in the UI. To display the rules in the UI, click the update configuration button, and then the rules will be synchronized from the VPC vRouter to the database of the Cloud. Note: Inbound rule sets cannot be deleted.
Note: Inbound rule sets cannot be deleted. Note: If you set both CIDR and the security group, note that only the intersection of them can take effect.
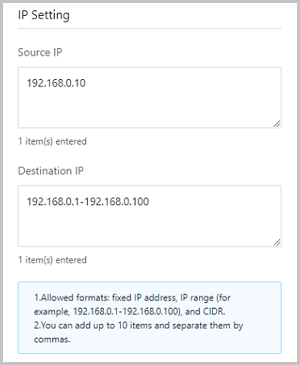
Note: If you set both CIDR and the security group, note that only the intersection of them can take effect.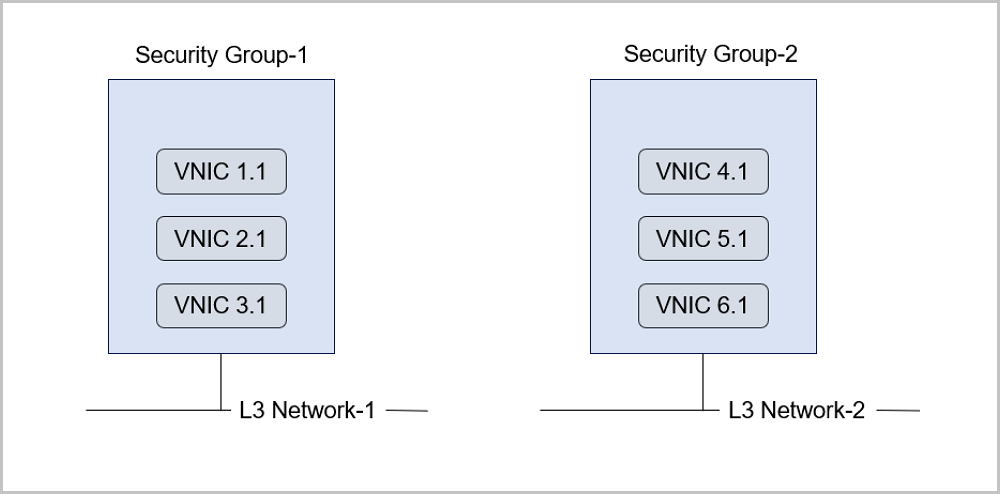
The basic workflow of using a security group is as follows: Select an L3 network, set the corresponding security group rule, and add specified VM instances to the rule.
 Note: You can add more than one L3 network of the same type at a time, but cannot add multiple L3 networks of different types.
Note: You can add more than one L3 network of the same type at a time, but cannot add multiple L3 networks of different types.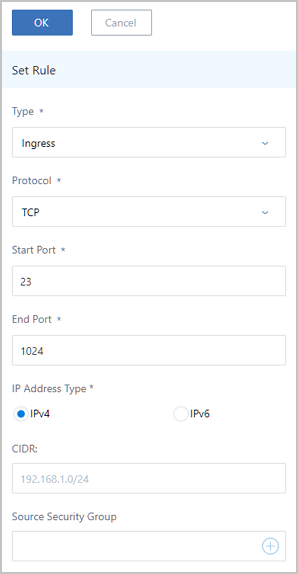
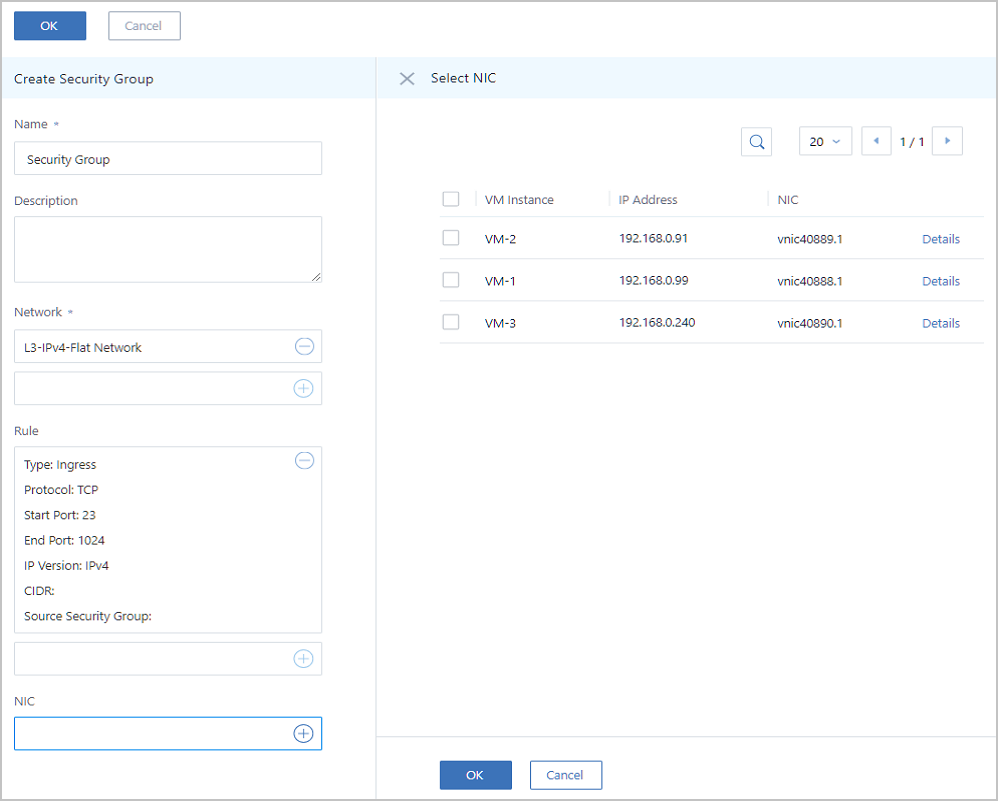
Assume that you add a VM NIC directly when you create a security group. On the Create Security Group page, click the Plus sign (+) in the NIC section. On the displayed Select NIC page, select the target VM instance.
Back to Top
Email Us
contact@zstack.ioEmail Us
contact@zstack.ioEmail Us
contact@zstack.ioThe download link is sent to your email address.
If you don't see it, check your spam folder, subscription folder, or AD folder. After receiving the email, click the URL to download the documentation.Thank you for using ZStack products and services.
Submit successfully.
We'll connect soon.Thank you for using ZStack products and services.